Here at Carden IT Services, we’ve built and implemented disaster recovery and business continuity plans for both large and small companies, and although the details change depending on each of our customers’ specifics, there is a set of essentials that every disaster recovery plan needs. (more…)
5 Ways Carden IT Services Helps You Secure Your Network
The more connected modern businesses become, the more important cybersecurity is to their success and survival. At Carden IT Services, we take the security of our clients’ hardware, software, and devices seriously. Here are 5 of the tools and techniques we use to keep them safe.
How Cloud Disaster Recovery Planning Makes You More Prepared
Business disasters can strike at any time. Whether it’s an office fire that destroys your hardware, a flood which prevents you accessing your workplace, or a ransomware attack which encrypts your data – anything which brings your business to a halt can have a long-lasting impact on your profits and your reputation if you are unable to meet your customers’ needs. Recovering from these disasters quickly, and with no data loss can be the difference between your company surviving or going out of business. (more…)
7 Reasons Why You Need Managed IT Services
Today, almost every aspect of a modern business is connected to the internet and so managed IT services have gone from being an advantage for businesses to being an absolute necessity. Here are 7 reasons why your business needs managed IT services. (more…)
Windows 11 – What You Need To Know
Microsoft recently announced the upcoming release of Windows 11. It has been over 6 years since a full, numbered release of Windows and there are several improvements to both the front and back-end of the Windows platform coming in the latest version.
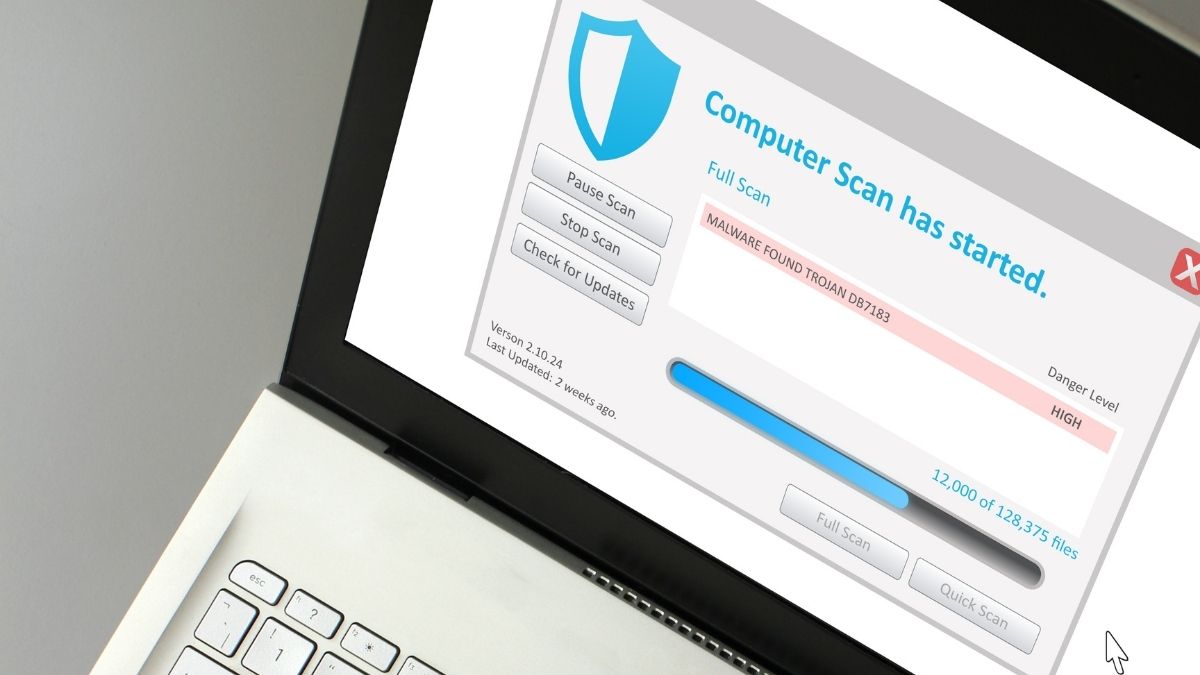
Vulnerability Scanning – What It Is & Why You Need It
Vulnerability scanning uses software to scan for vulnerabilities in a computer and networks. Many applications have critical security flaws in them which can leave your entire network at risk. Before, they were addressed by security patches, recent vulnerabilities in Zoom have allowed hackers to remotely control user’s PCs and flaws in Adobe Reader’s code allowed malicious code to be executed on Windows user’s machines. (more…)
Why Network Security Is Important
Network security involves adopting preventative actions to secure your network and its underlying infrastructure against the infiltration of ransomware and malware, the exfiltration of sensitive data, or potential damage to your ability to continue operating. When your network isn’t secure, your data and your customers’ data are at risk of being breached. This can have financial, reputational, and regulatory consequences. (more…)
What Businesses Thinking Of Moving To The Cloud Need To Consider
Many organisations in the United Kingdom are moving all or part of their IT network to the cloud. But what are the advantages? What are the risks? And what measures should you take before making the switch to a cloud environment? (more…)
Why You Should Avoid Cheap Laptops
With the recent rise in home working, many businesses are scrambling to supply their employees with laptops so that they can work effectively while away from the office. The first instinct can often be to buy the cheapest laptop available, especially if you are buying multiple machines at once. (more…)
How ThreatLocker Keeps Your Organisation’s Data Safe
More and more businesses are shifting to a full- or part-time home working. At the same time ransomware attacks, phishing attempts, data breaches, and dark web leaks are becoming more prevalent. That’s why it is more important than ever to have full visibility and control over what company data is being accessed, by who, and where from. (more…)